Terms
|
Configuration Management
Configuration Management is a systems engineering process for establishing and maintaining consistency of a product's performance, functional, and physical attributes with its requirements, design, and operational information throughout its life. |
|
|
Connected Retail
Connected retail means seamlessly connecting with customers via personalized marketing, the combination of a physical store and digital experience, supply chain, and multiple payment methods. |
|
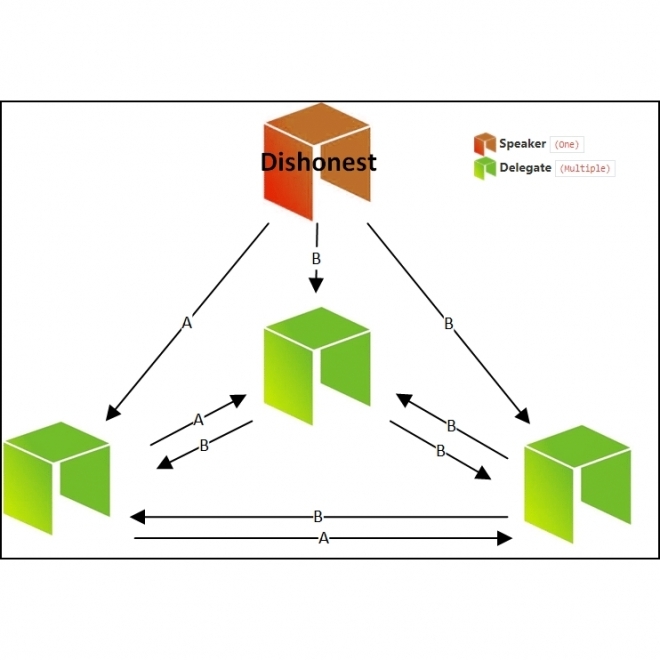 |
Consensus
Consensus makes sure all the ledgers have the exact same copy of the particular Blockchain history. This is realized when all network participants agree on the validity of the transactions. |
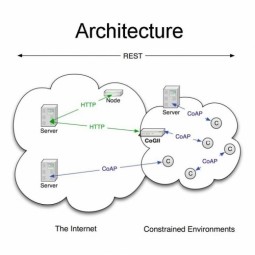  |
Constrained Application Protocol
Constrained Application Protocol (CoAP) is a specialized Internet Application Protocol for constrained devices, as defined in RFC 7252. It enables those constrained devices called "nodes" to communicate with the wider Internet using similar protocols. |
  |
Construction Operations Building Information Exchange
The Construction Operations Building Information Exchange (COBie) approach simplifies the capture and recording of building project handover data, basically by entering things like serial numbers as the project progresses. |
|
Container
In computer science, a container stands for an executable unit of software in which application code is packaged, along with its libraries and dependencies, in common ways so that it can be run anywhere, whether it be on a desktop, traditional IT, or the cloud. |
|
  |
Context-Aware Automation and Decision Optimization
Context-Aware Automation and Decision Optimization refer to monitoring unknown factors (environmental, interaction between machines and infrastructures, etc.) and having machines make decisions that are as “human-like” as possible. |
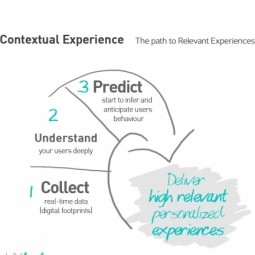  |
Contextual Experiences
Big data analytics solutions, combined with the proliferation of edge devices collecting highly contextual data, are allowing businesses to craft experiences that are unique for each user. |
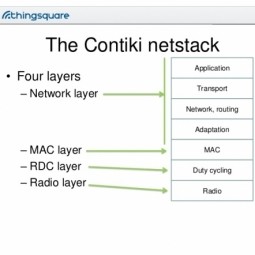  |
Contiki
Contiki is an open source operating system for networked, memory-constrained systems with a particular focus on low-power wireless Internet of Things devices. |
  |
Controller
A controller, in a computing context, is a hardware device or a software program that manages or directs the flow of data between two entities. In computing, controllers may be cards, microchips, or separate hardware devices for the control of a peripheral device. |
  |
Controller Area Network
A Controller Area Network (CAN) is a robust vehicle bus standard designed to allow microcontrollers and devices to communicate with each others' applications without a host computer. |
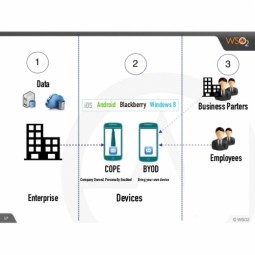  |
Corporate Owned, Personally Enabled
Corporate Owned, Personally Enabled (COPE) is a business model in which an organization provides its employees with mobile computing devices and allows the employees to use them as if they were personally-owned notebook computers, tablets, or smartphones. |
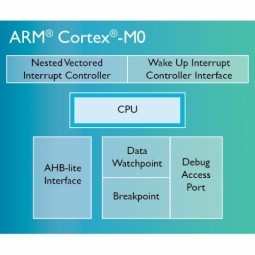  |
Cortex-M
Cortex-M is a family of microprocessors developed by ARM, which is mainly used in microcontrollers. They range from the cheapest M0 processor up to the Cortex-M4, which is used for effective digital signal control. |
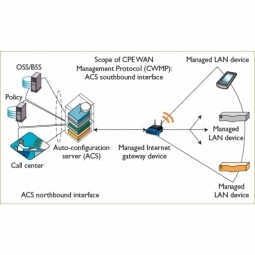  |
CPE WAN Management Protocol
CPE WAN Management Protocol (CWMP) is a protocol for communication between a CPE and Auto-Configuration Server that encompasses secure auto-configuration as well as other CPE management functions within a common framework. |
  |
CR2032 battery
A battery rated at 3.0 volts is commonly used in watches, wireless doorbells, and other small devices. Sometimes referred to as a “button cell” or “lithium coin,” the battery is shaped like a coin with dimensions of 20mm diameter x 3.2mm height (from which the “2032” is derived). |
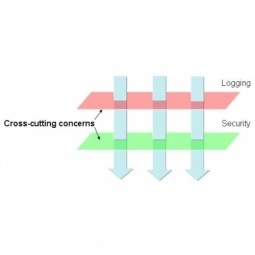  |
Cross-cutting Concern
Concern that affects the whole system and thus may impact multiple layers of the architecture. In aspect-oriented software development, cross-cutting concerns are aspects of a program that affect other concerns. |
 |
Cryptocurrency
Cryptocurrency is an alternative, digital, and virtual currency that uses cryptography to process and control transactions, as well as to create new units. |
  |
Cryptography
The practice and study of techniques for secure communication in the presence of third parties called adversaries. Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions. |
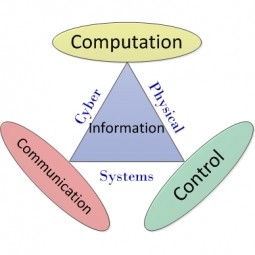  |
Cyber Physical Systems
A cyber-physical system (CPS) is a system of collaborating computational elements controlling physical entities. The systems often include some form of sensor which can transfer attributes from the real world to the digital sphere. |
  |
Cybersecurity Threat
In computer security, a threat is a possible danger that might exploit a vulnerability to breach security and thus cause potential harm. A threat can be either "intentional" (e.g., an individual cracker or a criminal organization) or "accidental" (e.g., the possibility of a computer malfunctioning. |
  |
DALI
DALI is a standardized interface for lighting control. Electronic ballasts for fluorescent lamps, transformers, and sensors of lighting systems communicate with the building automation and control system via DALI. |
  |
Dash 7
DASH7 is an “instant-on,” long-range, low power wireless communications standard for applications requiring modest bandwidth like text messages, sensor readings, or location-based advertising coordinates. |
  |
Data Aggregation
Data aggregation is any process in which information is gathered and expressed in a summary form for purposes such as statistical analysis. A common aggregation purpose is to get more information about particular groups based on specific variables such as age, profession, or income. |
  |
Data at Rest
Data at rest is an information technology term referring to inactive data that is stored physically in any digital form (e.g., databases, data warehouses, spreadsheets, archives, tapes, off-site backups, mobile devices, etc.). |
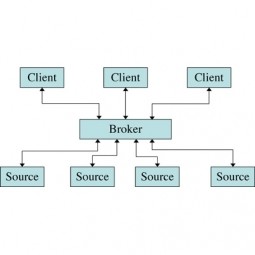  |
Data Broker
A data broker, also called an information broker or information reseller is a business that collects personal information about consumers and sells that information to other organizations. |
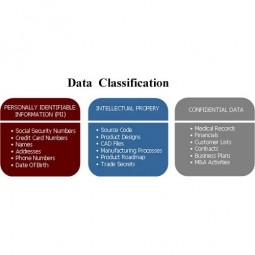  |
Data Classification
Data classification is the process of sorting and categorizing data into various types, forms, or any other distinct class. Data classification enables the separation and classification of data according to data set requirements for various business or personal objectives. |
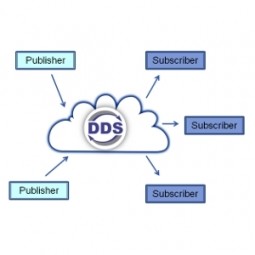  |
Data Distribution Service
The Data Distribution Service (DDS) for real-time systems is an Object Management Group (OMG) machine-to-machine standard that aims to enable dependable, high-performance, interoperable, real-time, scalable data exchanges using a publish-subscribe pattern. |
  |
Data-Driven Decision Management
Data-Driven Decision Management (DDDM) is an approach to business governance valuing decisions that can be backed up with verifiable data. The data-driven approach is gaining popularity within the enterprise as the amount of available data increases in tandem with market pressures. |
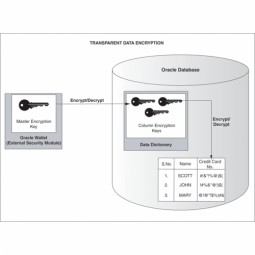  |
Data Encryption
Data Encryption is a process of encoding a message so that it can be read-only by the sender and the intended recipient. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. |
  |
Data Governance
Data governance refers to the overall management of the availability, usability, integrity, and security of the data employed in an enterprise. A sound data governance program includes a governing body or council, a defined set of procedures, and a plan to execute those procedures. |
