Terms
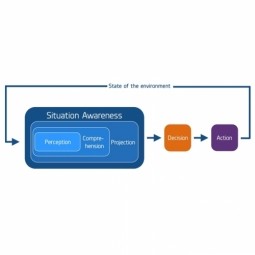  |
Situation Awareness
A field of study concerned with the understanding of the environment critical to decision-makers in complex, dynamic areas. Cyber situation awareness tools/techniques will need to be developed to enable IoT-based infrastructures to be monitored. |
  |
Smart Cards
A smart card is a device that includes an embedded integrated circuit chip (ICC) that can be either a secure microcontroller or equivalent intelligence with internal memory or a memory chip alone. |
  |
Smart Contract
A computer protocol that facilitates, verifies and/or enforces the negotiation or performance of a contract. Smart contracts allow the performance of transactions without the need for 3rd parties. |
  |
Smart Data
Smart data is digital information that is formatted so it can be acted upon at the collection point before being sent to a downstream analytics platform. If Big Data is the oil of the future, then Smart Data is the fuel that drives the production of the future. |
  |
Smart Factory
A smart factory is a learning factory, where people leverage data and technology constantly. Essentially, it is the implementation of Industry 4.0 technology. |
  |
Smart Manufacturing
Smart Manufacturing aims to reduce manufacturing costs from the perspective of real-time energy management, energy productivity, and process energy efficiency. |
  |
Smart Meters
A smart meter is usually an electronic device that records consumption of electric energy in intervals of an hour or less. It communicates that information at least daily back to the utility for monitoring and billing. |
  |
Smart Sensors
A smart sensor is a device that takes input from the physical environment and uses built-in compute resources to perform predefined functions upon detection of specific input and then process data before passing it on. |
  |
Social Machines
Web-based socio-technical systems in which the human and technological elements play the role of participant machinery with respect to the mechanistic realization of system-level processes. |
  |
Social Web of Things
The socialization of the Internet of Things is the integration of connected things into social life. For example, TV not only informs you that your favourite TV show is on in an hour but also lets you know which of your friends like the show, so it is possible to meet up and watch together. |
  |
Software as a Service
A subscription-based model where a monthly fee is charged for using software, rather than an upfront purchase. Software as a Service (SaaS) allows organizations to access business functionality at a cost typically less than paying for licensed applications. |
  |
Software-Defined Network
An approach to network management that decouples control of information flow from the hardware and gives it to a software controller. Software-Defined Network (SDN) allows for fewer data to travel wirelessly, making it a strategy for IoT networks services by abstracting lower-level functionality. |
 |
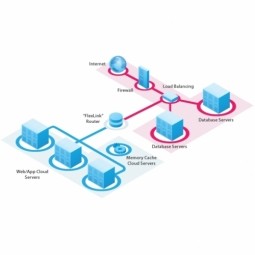
Software Development Kit
A Software Development Kit (SDK) consists of a group of development tools used to build an application for a specific platform. Typically, an SDK includes a visual screen builder, an editor, a compiler, a linker, and sometimes other facilities. |
  |
Steel Collar
Things in the workplace that replace or augment human labour. A “steel-collar workforce” is capable of tirelessly and efficiently performing repetitive tasks or monitoring. |
  |
Structured Data
A model that organizes data elements and standardizes how the data elements relate to one another. This includes data contained in relational databases and spreadsheets. |
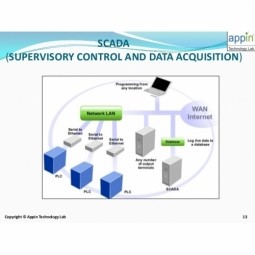  |
Supervisory Control and Data Acquisition
Supervisory Control and Data Acquisition (SCADA) is an industrial control system typically used for geographically dispersed assets, often scattered over large distances. It is for process control, the gathering of data in real time from remote locations in order to control equipment and conditions. |
  |
System Autonomy
System autonomy is an ability of an intelligent system to independently compose and select among different courses of action to accomplish goals based on its knowledge and understanding of the world, itself, and the situation. |
  |
System Configuration
A system configuration in systems engineering defines the computers, processes, and devices that compose the system and its boundary. A properly-configured system avoids resource-conflict problems and makes it easier to upgrade a system with new equipment. |
  |
System Environment
System environment is a context determining the setting and circumstances of all interactions and influences with the system of interest. The system environment includes developmental, technological, business, operational, organizational, economic, regulatory, ecological and social influences. |
  |
System on a Chip
A system on a chip (SoC) is an integrated circuit (IC) that integrates all components of a computer or other electronic system into a single chip. SOC's may contain digital, analog, mixed-signal, and often radio-frequency functions―all on a single chip substrate. |
  |
System on a Module
A system on a module (SOM) is a board-level circuit that integrates a system function in a single module. It may integrate digital and analogue functions on a single board. A typical application is in the area of embedded systems. |
  |
Telehash
Telehash is a peer to peer data distribution and communication protocol that is designed to be decentralized and secure. Telehash is also a set of implementations of the protocol which is still in heavy development |
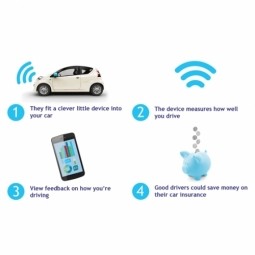  |
Telematics
An IT concept regarding the long-distance transmission of data. Telematics includes anything from GPS systems to navigation systems. In vehicles on the move, telematics refers to the integrated use of telecommunications and informatics that show the vehicles current position on a map. |
  |
Tensorflow
TensorFlow is an open source software library for numerical computation using data flow graphs. Nodes in the graph represent mathematical operations, while the graph edges represent the multidimensional data arrays (tensors) communicated between them. |
  |
Terabyte (10^12 byte TB)
The terabyte is a multiple of the unit byte for digital information. The prefix tera represents the fourth power of 1000, and means 1012 in the International System of Units (SI), and therefore one terabyte is one trillion (short scale) bytes. |
  |
Thingbot
A thingbot is something with an embedded system and an Internet connection that has been coopted by a hacker to become part of a botnet of networked things. |
  |
Things as a Service
The concept of delivering IoT functionality without the end-user having to operate or maintain extensive hardware, e.g. services such as Hadoop can be delivered in the cloud to receive and process the data generated by IoT-enabled sensor networks. |
  |
Threat Analysis
Threat analysis is an essential step in identifying the probability of terrorist attack and results in a threat assessment. The examination of threat sources against system vulnerabilities to determine the threats for a particular system in a particular operational environment. |
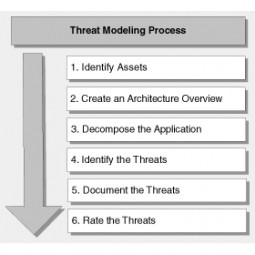  |
Threat Modeling
Threat modeling is an approach for analyzing the security of an application. It is a structured analysis to identify, quantify, and address the information security risks associated with an application or a system. |
  |
Tilt Sensing
A MEMS concept referring to the measurement of the inclination or angle of change with respect to gravity. Typical applications include industrial equipment platform stabilization and landscape/portrait detection on handheld devices. |
